Strengthening Your ISMS: Strategies to Guard Against Malware
Malware attacks are a dangerous threat to consumers and businesses equally, infiltrating computer networks, pilfering confidential data, and disrupting operations, bringing loss of financial resources, along with data loss, and potential extortion. Effective malware prevention and defence are absolutely critical to protect personal information, financial data, and even precious memories. The consequences are even worse for organizations, government, and businesses, as successful compromises can be disastrous to operations and confidential information.
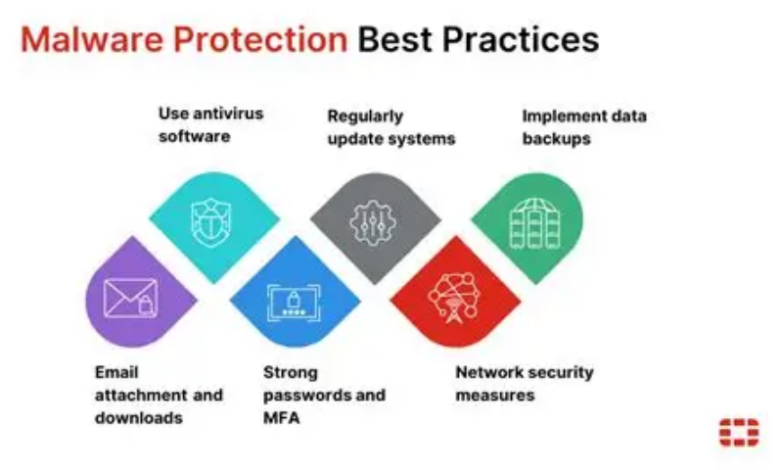
How Can You Prevent Viruses and Malicious Code?
- Install Safety Software- To protect your organization’s data from malware attacks and other threats, install information security management software. Update it regularly, or set it to update automatically, with the best protection.
- Recognize Threats- Scammers send phishing emails deceptively, which prompt you to click on a link or open an attachment that installs malware. Don’t click on a link in an unexpected email. Do not dial that number. Instead, dial the company with a number or site you have determined to be real. Scammers create false security pop-ups that tell you to make a call to a phone number for technical support. If you do make the call, they ask to have remote access to your computer, conduct a fake diagnostic test, and then charge you to fix a problem that does not exist. Never dial a number that appears in a pop-up. If you see an advertisement for software that interests you, don’t click the ad. Instead, access the site by typing in the address.
- Avoid Risks- Avoid the use of items that might expose you to malware. Avoid using untrusted websites to download free items like music, films, television shows, or games. Avoid downloading material through peer-to-peer (P2P) file-sharing sites. Scan USB thumb drives, external drives, and other external devices with an antivirus or security software before opening them.

What is the Role of ISMS in Protecting Information?
Information Security Management Systems is an efficient system established to safeguard sensitive information to ensure the confidentiality, integrity, and availability of data in an organization.
- Security of Sensitive Information- ISMS is crucial for protecting sensitive information in an organization. Through the implementation of robust security controls, access controls, and encryption, it ensures the confidentiality of sensitive data by keeping it away from unauthorized usage or disclosure.
- Risk Mitigation and Management- Risk management is among the main implications of the Information Security Management System software. With ISMS, an organization can identify information security risks, assess them, and minimize them. Organizations can implement proper controls to counter threats and vulnerabilities so as to lessen the impact of the risks and make the business more robust overall.
- Regulatory Compliance- Under today’s regulatory environment, adherence to legislation and standards is of utmost significance. ISMS provides an organized framework to organizations for aligning their information security practices with regulatory needs. Compliance with data protection law, industry standards, and other regulatory compliance is not only legally mandated but also assists the organization in attaining credibility and trust.
- Business Continuity and Business Resilience- ISMS is a significant factor in business resilience and business continuity. By identifying and addressing probable information system interruption points, organizations can enable the availability and usability of critical processes. This business resilience is essential in maintaining smooth operations despite unexpected events, such as cyberattacks or natural disasters, minimizing downtime and cost loss.
- Enhanced Customer Trust and Reputation- Customer trust is critical to business success. ISMS comes into play here by ensuring that customer information is processed securely. When customers are confident that their data is secure, it makes them more confident in the organization. This subsequently enhances the reputation of the organization, resulting in long-term relationships with clients, partners, and stakeholders.

How to Implement an Information Security Management System?
The implementation of an Information Security Management System (ISMS) is not one-size-fits-all. Each organization has special data security requirements, compliance needs, and threat environments. Therefore, successful implementation must be well-planned, made-to-measure, and conscientiously maintained. The process would typically involve the following primary steps:
- Define Objectives- The foundation for any ISMS is setting its objectives. Organizations must determine what information needs to be safeguarded and why. This entails identifying sensitive data, regulatory compliance, and business areas of risk. Whether the objective is to attain compliance with regulations, safeguard customer data, or maintain business continuity, a defined objective guarantees all the other components of the ISMS framework.
- Conduct a Risk Assessment- A thorough risk assessment must be done to realize potential threats and vulnerabilities. This involves identifying the risks internal and external, such as cyberattack, insider attack, loss of data, and natural disasters. Organizations need to categorize risks based on their potential impact and probability to ensure security controls are implemented to prevent the most critical threats.
- Implement Security Controls- Once risks have been identified, organizations must select and implement appropriate security controls. They may be technical (e.g., encryption, firewalls), administrative (e.g., access controls, policies), or physical (e.g., surveillance, secure facilities). Control selection should be done based on the risk assessment findings as well as best practices within an industry, e.g., ISO 27001 or NIST frameworks.
- Training and Awareness- The workers also have an important part to play when it comes to information security. Personnel ought to be periodically trained on security policy, best practices, and potential threats like phishing attacks. A security awareness culture avoids human errors that might compromise the ISMS.
What are the Benefits of ISMS?
ISMS provides a holistic perception of how to manage the information systems of an organization. This has numerous benefits, some of which are discussed below.
- Protects Sensitive Information- An ISMS protects any type of proprietary information assets, whether they are in paper form, stored electronically or in the cloud. They can protect personal data, intellectual property, financial data, customer information and data given to companies by third parties.
- Regulatory Compliance- ISMS makes sure that all contractual obligations and regulatory compliance needs are met by organizations and provides a clearer picture of legalities in information systems. Since violation of legal regulations carries substantial fines, an ISMS is especially helpful in those extremely tightly controlled sectors with critical infrastructures, such as finance or healthcare.
- Support Business Continuity- Whenever organizations adopt an ISMS, they automatically improve their protection against risks. This reduces the number of security breaches, such as cyberattacks, in fewer terms of incidents, therefore fewer disruptions and downtime, which are essential to allow business continuity.
- Reduces Spending- An ISMS gives a detailed risk analysis of all the assets. This enables the companies to choose the riskiest assets so as to save money on unnecessary defence carelessly, and provides a purposeful approach towards their safeguarding. This disciplined approach, with minimal downtime due to fewer security incidents, significantly lowers an organization’s total spending.
- Enhances Company Culture- ISMS provides a total approach to security and asset management within the organization and is not limited to IT security. This encourages all employees to understand the risks related to the information assets and apply best practices in security in their day-to-day work.
Conclusion
Implementing effective malware protection procedures is not just a personal responsibility but also a corporate imperative. These procedures protect the integrity of personal information, financial assets, and mission-critical data. For corporations, these procedures impact the bottom line directly, sin



